Israeli surveillance software Pegasus targets cloud data on infected iPhones

Israeli fellowship NSO Group claims its updated multi-million dollar surveillance tool, called Pegasus, tin instantly also extract information from cloud services similar iCloud, Google Drive together with Facebook Messenger, alongside others, from an infected iPhone or Android smartphone.
According to a paywall’d study published yesterday past times The Financial Times, the app plant on the latest iPhone together with Android smartphones, taking payoff of exploits to proceed working fifty-fifty later on the tool has been removed past times the user.
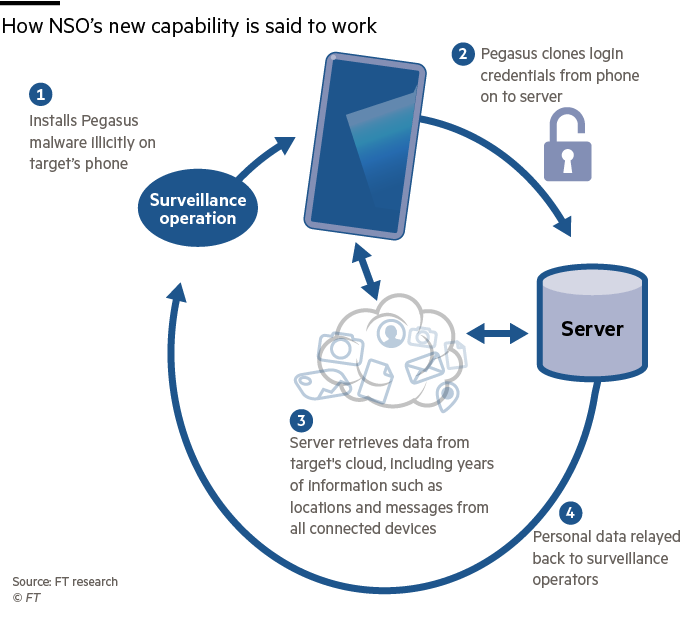
The novel technique is said to re-create the authentication keys of services such equally Google Drive, Facebook Messenger together with iCloud, alongside others, from an infected phone, allowing a dissever server to together with thus impersonate the phone, including its location. This grants open-ended access to the cloud information of those apps without ‘prompting 2-step verification or alarm electronic mail on target device’, according to 1 sales document.
Stealing authentication tokens is an onetime technique of gaining access to someone’s cloud trace of piece of job concern human relationship without needing their user name, password or two-step verification codes. Unlike the encryption keys iOS uses to secure your local data, these authentication tokens are non stored inwards Apple’s Secure Enclave which is walled off from the balance of the system.
Here’s Apple’s response:
iOS is the safest together with most secure computing platform inwards the world. While approximately expensive tools may be to perform targeted attacks on a really small-scale issue of devices, nosotros create non believe these are useful for widespread attacks against consumers.
Curiously, Apple doesn’t deny such a capability could exist. The tech giant added that it regularly updates its mobile operating arrangement together with safety settings to maintain users protected.
While NSO Group denied promoting hacking or mass-surveillance tools for cloud services, it didn’t specifically deny it’d had developed the capability described inwards the documents.
Crucially, the tool plant on whatever device “that Pegasus tin infect”.
One pitch document from NSO’s nurture company, Q-Cyber, which was prepared for the authorities of Republic of Uganda before this year, advertised the powerfulness of Pegasus to ‘retrieve the keys that opened upward cloud vaults’ together with ‘independently sync-and-extract data’.
Having access to a ‘cloud endpoint’ agency eavesdroppers tin accomplish ‘far together with inwards a higher house smartphone content’, allowing information well-nigh a target to ‘roll in’ from multiple apps together with services, the sales pitch claimed. It is non nevertheless clear if the Ugandan authorities purchased the service, which costs millions of dollars.
Take NSO Group’s claims with a grain of salt.
This isn’t the kickoff fourth dimension someone made bold claims equally to bypassing the safety features of Apple’s custom-designed chips together with the iOS software powering iPhone together with iPad. It’s truthful that constabulary enforcement doesn’t shy away from paying millions of dollars inwards fees for rights to exercise such software. It’s also truthful that the FBI eventually turned to Pegasus in guild to unlock a telephone belonging to the San Bernardino shooter. However, it’s also truthful that this was an older iPhone without Apple’s Secure Enclave cryptographic coprocessor which provides total disk encryption together with hardware protections for the disk encryption keys.
Yet, tools similar Pegasus might bring been used to hack fifty-fifty modern iPhones, precisely that’s because their owners were foolish plenty to install a rogue app that included malware. Other techniques include installing an invisible VPN to sniff network traffic, non bad a weak passcode or exploiting a major oversight on a user’s purpose which tin opened upward an laid on vector.
It doesn’t await similar Pegasus exploits an iOS vulnerability to larn to your cloud data.
One of the pitch documents offered an old-fashioned way to thwart this sort of eavesdropping: changing an app’s password together with revoking its login permission. That cancels the viability of the replicated authentication token until, according to the document, Pegasus is redeployed.
Yes, iOS exploits create be together with approximately of them larn never disclosed, precisely Apple’s aggressive software update machinery installs patches swiftly. To my knowledge, no safety fellowship has nevertheless to claim unambiguously that it tin hack into the latest iPhones.
Pegasus was of late used to hack WhatsApp via an undisclosed vulnerability. WhatsApp has since unopen the loophole together with the U.S.A. Department of Justice is investigating.
Thoughts?
0 Response to "Israeli surveillance software Pegasus targets cloud data on infected iPhones"
Post a Comment