An unpatched macOS vulnerability lets malware completely bypass Gatekeeper security
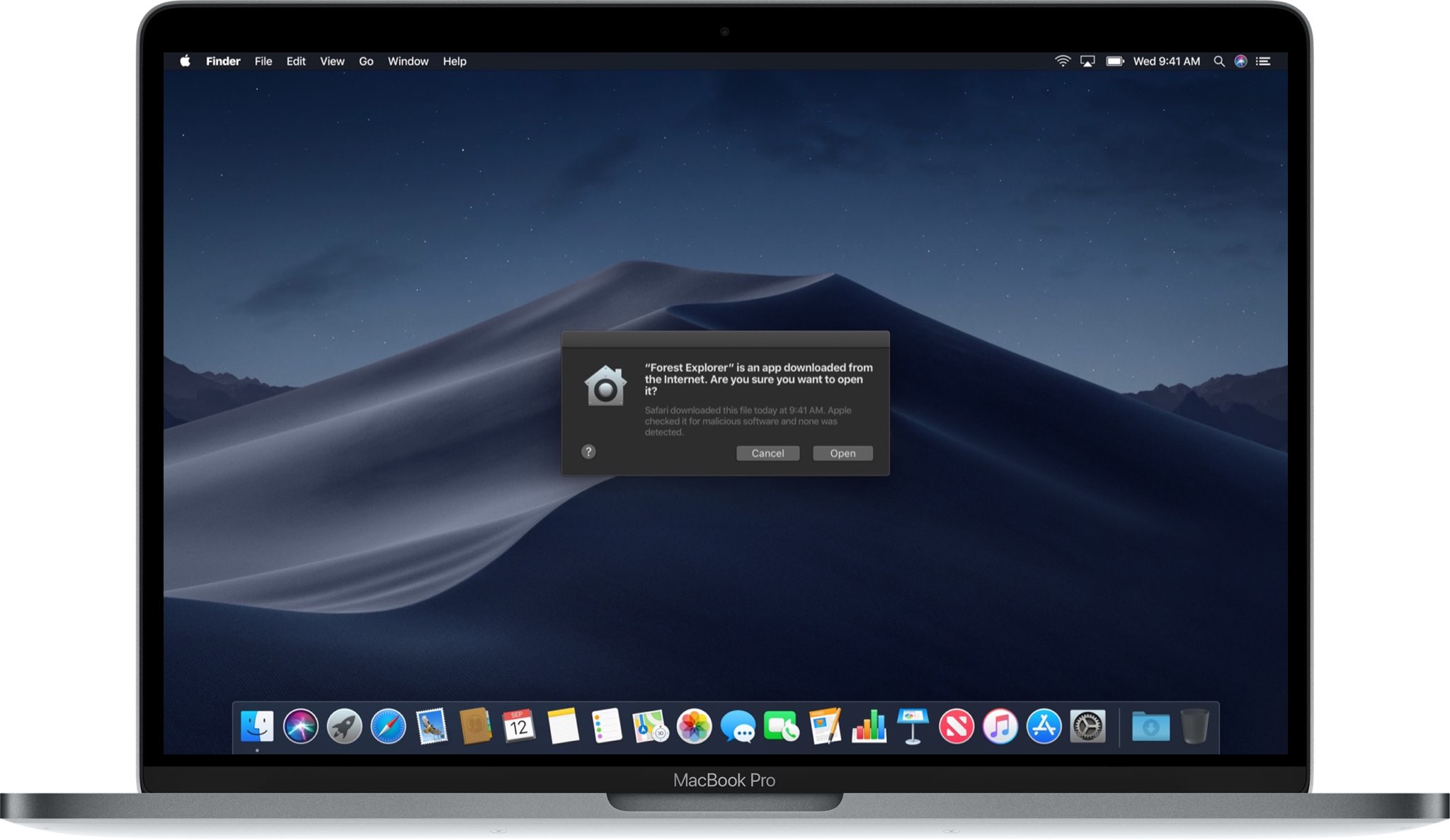
An unpatched vulnerability inward macOS Mojave permits attackers to completely bypass the Gatekeeper safety feature. Apple was initiative off informed virtually the flaw on Feb 22, simply last week’s macOS 10.14.5 update hasn’t fixed the vulnerability fifty-fifty though it was supposed to.
Gatekeeper is a safety characteristic of macOS that enforces code signing too verifies downloaded apps earlier y'all opened upwards them, which reduces the likelihood of inadvertently executing malware.
According to safety researcher Filippo Cavallarin who discovered too reported this safety oversight inward macOS to Apple, via AppleInsider, a rogue app would exploit the fact that Gatekeeper considers both external drives too network shares every bit “safe locations.” As a result, whatever app executed from these locations volition run without Gatekeeper’s intervention.
Here’s a video showing proof-of-concept inward action.
By combining this Gatekeeper blueprint amongst a twosome of legitimate features inward macOS, a rogue political party could completely modify the intended guide of Gatekeeper, the researcher cautioned.
Okay, what are the 2 legit features?
The initiative off legit characteristic is automount (also known every bit autofs) that lets y'all automatically mountain a network portion past times accessing a especial path—in this case, whatever path commencement amongst ‘/net/’. The minute legit characteristic is that ZIP archives tin comprise symbolic links pointing to an arbitrary place (including ‘automount’ endpoints) too that macOS’s unarchiver doesn’t perform whatever banking concern gibe on the symlinks earlier creating them.
How virtually about illustrative representative of how this exploit truly works?
Let’s regard the next scenario: an assaulter crafts a ZIP file containing a symbolic link to an automount endpoint they command (for example, Documents -> /net/evil.com/Documents) too sends it to the victim. The victim downloads the malicious archive, extracts it too follows the symlink.
This is terrible, most people can’t distinguish symlinks from existent files.
Now the victim is inward a place controlled past times the assaulter simply trusted past times Gatekeeper, thence whatever attacker-controlled executable tin run without whatever warning. The fashion the Finder is designed to shroud app extensions too the amount file path inward window titlebars makes this technique real effective too difficult to spot.
Cavallarin says Apple stopped responding to his emails later beingness alerted of the number on Feb 22, 2019. “Since Apple is aware of my ninety days disclosure deadline, I brand this data public,” he wrote on his blog.
Related
No ready is available every bit of yet.
Apple volition almost for sure fpatchx this flaw inward the adjacent update. Until then, a possible workaround is to disable the “automount” characteristic according to the instructions provided at the bottom of Cavallarin’s weblog post.
Have y'all been affected past times this vulnerability?
If so, we’d similar to ask heed your thoughts inward the comments!


0 Response to "An unpatched macOS vulnerability lets malware completely bypass Gatekeeper security"
Post a Comment