An Inside Look Into a Recent Spam Operation
Millions of people were affected for 10 days in March by a spam email operation. But the spammer didn’t set a password for their server (via TechCrunch).
[Apple Support Scam is a new Voice Phishing Trick]
Email Spam
It’s a fascinating story. Security researcher Bob Diachenko found the server after the operation. The spammer had moved on but the server was ready to be used again. With TechCrunch‘s help, the hosting provider—Awknet—pulled the server offline.
In a copy of one of the spam emails, it redirected people through several websites in an attempt to figure out their location based on their IP address. For U.S. residents, people were sent to a fake CNN website promoting a fake health remedy. For U.K. residents, it was a fake BBC site promoting a bitcoin scam.
Related
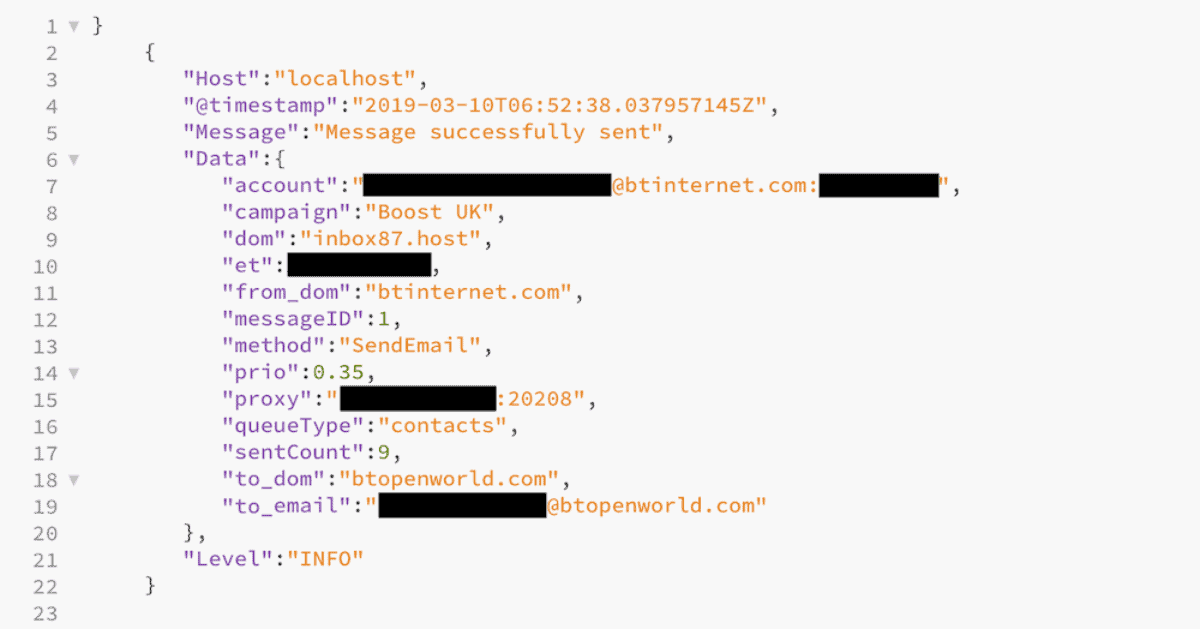
With stolen email addresses, the spammer was able to make it look like the email was sent from a person in a victim’s contact list. Each message was routed through proxy servers made up of several cell phones hundreds of times a second.
From March 8 to March 18, about 5.1 million emails were sent with 162,980 people clicking the spam email. The database was shared with Troy Hunt, so you can see if your email was leaked using HaveIBeenPwned.com.
[iOS: Enable Do Not Disturb to Block Spam Calls]

0 Response to "An Inside Look Into a Recent Spam Operation"
Post a Comment