The Punycode Phishing Attack on Web Browsers Ain’t So Puny
There’s another phishing threat out there, a particularly nefarious one that takes advantage of how similar some foreign characters appear compared to our own alphabet. A web application developer has provided a proof-of-concept of the vulnerability using Apple’s domain name, or something that strongly resembles it when you realize that not all computers use just ASCII characters. What results is the Punycode phishing attack.

Through a Punycode phishing attack, you could be tricked into thinking you’re on a major retailer’s website (Image Credit: Geralt)
ASCII Versus Unicode
The abbreviated form of American Standard Code for Information Exchange is ASCII. It’s a way of representing text in computers. telecommunications equipment, and other devices. It was first developed from telegraph code, and it’s fairly limited in terms of which characters it can represent. In total, ASCII is capable of rendering 128 characters, which have to encompass not only the lower-case and upper-case letters of the alphabet, but also every numerical digit, commonly-used symbol (like &, $, #, @, etc.).
ASCII also includes special characters like the delete key on your keyboard, the carriage return, and many others. To make a long story short, the limitations of ASCII do not make it possible to include accented characters like ä, é, î, or any similar variants. Needless to say, the letters of completely foreign scripts like the Cyrillic character set are completely out of the question.
That’s why we came up with Unicode. Unicode is a much broader character set, and encompasses more than 128,000 characters covering 135 modern and historic scripts, along with multiple sets of symbols.
What Does the Internet Use?
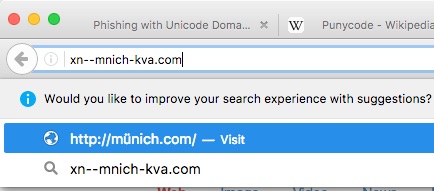
Internet host names use ASCII, for the most part. However, recognition of the need to accommodate foreign languages has resulted in the creation of Punycode – a way to represent Unicode within the limited character subset of ASCII used for Internet host names. Punycode provides the means to incorporate names like München (the German name for the city of Munich) in a domain name in such a way that German readers will recognize it as such. In Punycode, München is encoded as “xn–mnich-kva”. On a browser that renders Punycode into Unicode, such a domain as “xn–mnich-kva.com” would appear as “münich.com”, as you can see in the below screenshot from Firefox.
Up Next: A Phishing Attack Using Punycode
Page 2 – A Phishing Attack Using Punycode
The Punycode Phishing Attack
If all foreign characters looked so different from ASCII characters, we wouldn’t have any problems. However, that’s not the case, especially when you take into account the font choice used by some browsers. In Punycode, this:
xn--80ak6aa92e.com
is the equivalent of:
аррӏе.com
Notice the similarity to apple.com? This is because the Punycode is rendering the Cyrillic equivalent of “a” (U+0430) instead of ASCII’s “a” (U+0061). Chrome 57 and earlier, along with all versions of Firefox, use fonts that will make you see the domain name as “apple.com” and possibly fool you into thinking you’re at Cupertino’s website.

In the latest version of Firefox, I entered “xn-pple-43d.com” into my browser, and it turned into what looked like apple.com
The same problem exists in Windows in Internet Explorer and Edge, if the computer has Cyrillic font support.
Related
What’s Being Done to Fix It?
Security researchers reported this bug to Chrome and Mozilla (makers of Firefox) on January 20, 2017. Chrome fixed it as of version 58 on March 28, but that particular update is still rolling out to users. I actually received the new version of Chrome minutes after capturing a screenshot of the bug in action.
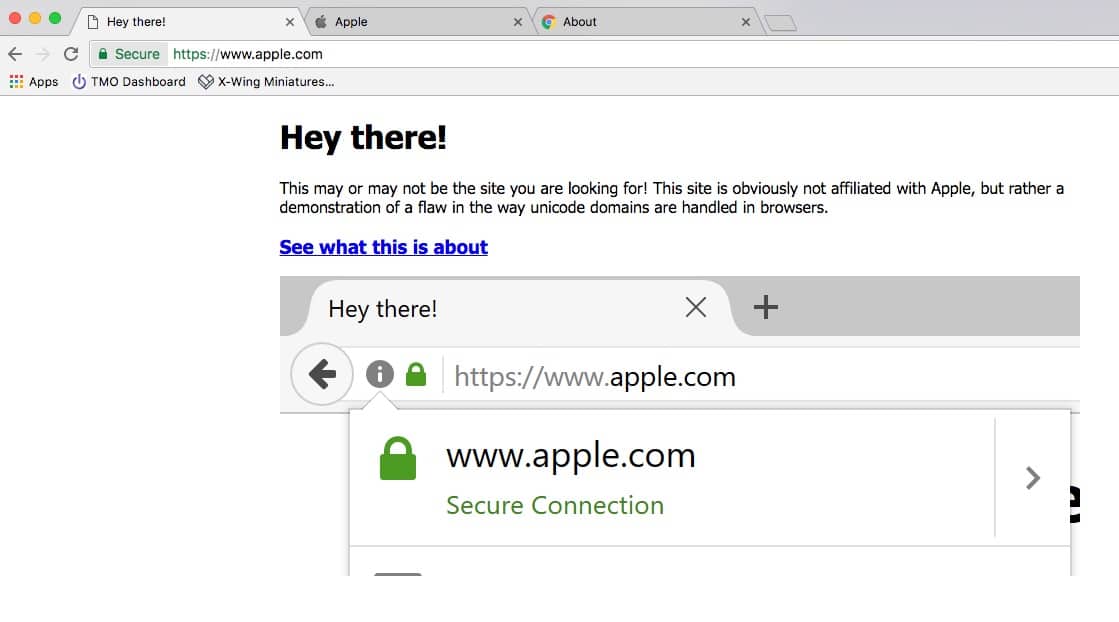
In Chrome 57, I entered “xn--80ak6aa92e.com” into my browser, and it turned into what looked like apple.com
The bug does not occur in Safari at all. Firefox, on the other hand, will always suffer from this bug, it seems. Developers at Mozilla have said such attacks cannot be detected programmatically, and that it is the responsibility of domain owners to identify such potential threats and register those Punycode domains themselves.
There is, however, a workaround in Firefox to resolve the issue. If you visit about:config and set network.IDN_show_punycode to true, Once done, Firefox won’t transcode Punycode into Unicode.
The Moral of the Story – Use Your Password Manager
The truth found in this is that you should be much more careful about entering personal information on a website. This is true even if it’s one you think you recognize and has an apparently-valid SSH certificate. To prevent falling prey to a Punycode phishing attack, rely heavily on your password manager to protect you. Punycode phishing attacks don’t fool password managers. Hopefully, Mozilla will soon reverse its stance on the issue, but at least there’s a way to protect yourself in Firefox. You should also be sure to upgrade Google Chrome, if you use it.

0 Response to "The Punycode Phishing Attack on Web Browsers Ain’t So Puny"
Post a Comment